
“The industrial internet of things is still a big mess when it comes to security.”
If that headline from business technology news outlet ZDNET doesn’t give industrial organizations pause, we don’t know what will. Stop for a moment and think of all the potential entry points the IIoT could allow within IT/OT operations.
- How vulnerable to attack are these systems?
- Could a cybercriminal gain unauthorized access?
- Is the organization’s data at risk for theft?
- Might ransomware make its way into the system and take control?
Citing a Barracuda cybersecurity analysis, ZDNET reported that “94% of industrial organizations experienced a ‘security incident’ during the past 12 months” with many organizations indicating that the attack had “significant” impact on their operations.1
These alarming findings are why we’ve spent a lot of time on this blog talking about cybersecurity and the IIoT—and we’re not done yet.
As the IIoT continues to grow, thanks to Industry 4.0, so, too, will the need to make cybersecurity the new normal for industrial, manufacturing, and commercial operations.
Here are 3 security-related things that organizations can do right now to help secure their IIoT-enabled systems and adopt the new normal.
-
Make a list and check it twice.
If there’s one thing cyberattacks have taught the industrial world, it’s that no one is immune. While it’s impossible to secure a network from attack 100%, that doesn’t mean organizations shouldn’t try.
One of the biggest mistakes industrial and manufacturing companies can make is to rely solely on their device manufacturers to ensure the security of their systems. While that may have been good enough in the past, the new normal requires organizations to increase their involvement and understanding of security at every turn.
A good first step is to make a list of all the IIoT-enabled products, devices, and sensors within the organization and rank them by which devices are secure, and which are not.
A similar tactic is to ask about security features, functions, and protocols when purchasing new devices. Security countermeasures are evolving just as rapidly as criminal activity.
-
Say ‘yes’ to updates.
Some of the best products on the market, including FieldServer, are designed for “set it and forget it” installation. But that doesn’t mean industrial organizations should sit back and take an “if it ain’t broke, don’t fix it” approach.
On the contrary. Protocol gateways also require security measures or else they’re vulnerable to attack. So, if and when a device manufacturer offers firmware updates, patches, and other upgrades, organizations would be wise to take advantage of them.
-
Add another layer of security.
Wouldn’t it be great to buy the latest and greatest devices to replace products that are more than a year or two old? Of course, it would!
For most organizations, though, that’s not the most efficient nor cost-effective way to do business or ensure security.
So, until the product is at the end of its useful life and is ready to be replaced with something more advanced and secure, organizations should consider adding a passthrough device like a FieldServer gateway solution. Our rigorously tested and secure gateways are an affordable and portable way to boost security among connected devices.
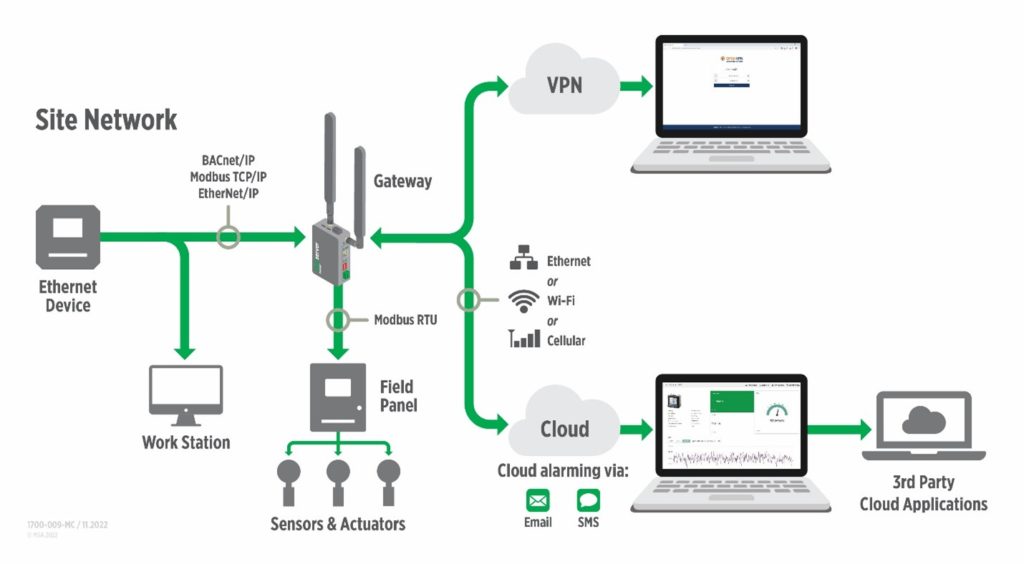
In fact, one of the reasons we’re so adamant about the security of our FieldServer gateways is because we offer secure connection within systems, at the edge, and to the Cloud.
Other devices offer an “either/or” connection, forcing a choice between the network or the Cloud. FieldServer, on the other hand, offers “both/and” protocol translation and connectivity for secure, encrypted data exchange via ethernet, serial, and cellular.
Conclusion
Cyberthieves are continually finding new ways to threaten the security of industrial and automation systems. That means organizations need to become more proactive in finding ways to strengthen security.
If your organization would like to learn more about the new normal for IIoT security, let’s talk. In addition to offering ODVA certified gateways, our cybersecurity experts can share more about the latest technologies, best practices, and strategies to better detect and protect against attacks.





